Not at all related to the 70s UK film series Confessions Of A… (sex comedies, thought of at the time as soft-core porn), an article over at The Register caught my attention. Before I get back to that, I’d never realised that John Le Mesurier (Dad’s Army star) was in Confessions Of A Windows Cleaner.
Anyway, back on track, I’ve closed the Wikipedia page so no more distractions… So, a systems admin (Trevor Pott) wrote a short article on how a couple of simple small things allowed a conficker infection to survive a cleaning purge on his network, and what he could have done differently (with hindsight, obviously) to prevent it.
Not particularly thrilling for most readers of this site, I understand, but the sort of train of logic and problem solving that I sometimes miss here in Kazakhstan.
Jun 10 2010
Confessions Of A SysAdmin
Comments Off on Confessions Of A SysAdmin
Jun 03 2010
Drinking A Can Of Guinness A Day
Back to Anna’s photos and videos once more. Once the blog has caught up with the UK clips and pictures, I’ll try and make sure those taken in Kazakhstan are posted quickly, and hopefully get close to real time publishing once more.
This one is very short, taken on the 22nd of February 2010. In the UK, there is a safe limit advised by the government, when it comes to how much alcohol you can drink a day. One can of normal strength beer isn’t a problem, however the size of the can might just have some sway in the decision making process, normally…
Comments Off on Drinking A Can Of Guinness A Day
Jun 03 2010
Step By Step New Hotmail Account Guide
If you are Roger (Dad’s next door neighbour), this post if for YOU! If you aren’t him, and are just reading this blog post because it is on the front page, feel free to keep reading if you need a step by step guide to starting a new Hotmail account. If I was in Evesham right now, I’d probably try and convince Roger that a GMail address might be a better idea, but that would take too long using Dad as a message relayer 🙂
Anyway, onto the guide.
1) Turn on the PC. Start your preferred internet browser (likely to be Internet Explorer, Firefox or Chrome)
2) Enter www.hotmail.co.uk in the address bar, and press Return or Enter on the keyboard
3) Click the Sign Up button located in the lower left of the screen
(Hoping a screen shot isn’t necessary here 🙂 )
4) Decide whether you want a @hotmail.co.uk or a @live.co.uk address. It makes NO differences, other than personal preference. If hotmail is your choice, proceed to step 5. If you want live.co.uk, click the first drop down box and click on live.co.uk
5) Pick an address you want to use. It makes sense to choose something that is difficult to mis-spell, easy to remember, and finally, something someone else will not have already registered. Bad choice examples: amateurastrologer@hotmail.co.uk , committed_drunkenness@live.co.uk , john.smith@hotmail.co.uk . All of those are either easy for other people to spell incorrectly, or will most likely have been registered already.
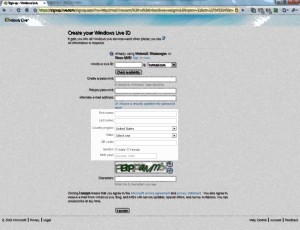
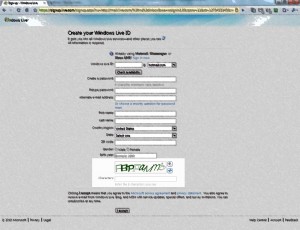
6) Enter your chosen e-mail address in the first text entry box. Click the check availability button. Swear loudly as you discover someone else already has the exact address you want. If it isn’t free, Microsoft will ask for your name and some relevant interests and suggest available e-mail addresses you might like. Either follow their steps, or click on the little X in the Windows Live ID advanced search box and type in a new e-mail address. Again click the check availability button. Repeat these step until you are informed that your chosen address is available. (If possible, try not to select an alternative address they offer that has a number on the end. Again, easy for other people to mis-type/remember it).
7) Select a password that you want to use to sign into this e-mail account. If possible, choose something you do NOT use anywhere else online. It needs to be six characters long, and if you use a mixture of lower and UPPER case letters, numbers and special characters (£${ etc. etc.) it will be harder for other people to guess your password and hack in. It will also make it more difficult for you to remember, so try and find a balance 🙂 Type this same password into the retype password box.
8) If you have now selected an e-mail address and password that Microsoft isn’t complaining about WRITE THEM DOWN NOW. TWICE. Keep each piece of paper in a different room, so if you ever forget your address or password, and can’t find the 1st piece of paper with the details recorded on, you have a second chance.
9) If you already have a different e-mail address that you can still access, enter it in the Alternate e-mail address box. This is the address that Microsoft will use if you ever ask to reset your password if you’ve forgotten it (and lost both pieces of paper). If you don’t already have an e-mail account, click the “Or choose a security question for password reset” link. If you clicked the link, select a question you won’t ever forget the answer to, and enter that answer in the Secret Answer box.
10) Fill in the rest of the boxes down to Birth Year with your relevant information.
11) In the text box below Birth Year, you need to type the eight characters shown in the image just above it. This is Microsoft’s attempt to make sure you are a real human asking for an e-mail address. They apparently had problems with hamsters and motorbikes pretending to be humanoid and asking for addresses. Or it could have been people using automatic systems for spamming. I can never remember which.
12) Untick the “Send me e-mail with promotional … ….” box. Double check all the boxes on the page are correctly filled in.
13) Click I accept. If all information has been entered correctly, you will now be logged into your e-mail account. The first time you send an e-mail, you may be asked to enter another eight letters from a strange looking image. Again, another anti-spam step.
14) In the future, visit hotmail.co.uk, and if you see your e-mail account on the right hand side, click sign in. Then enter your password, and click sign in. If you are on a different computer or internet browser, you will also need to enter your e-mail address.
15) Ideally, repeat steps 1-13 and create a second e-mail address that you will use when signing up for other accounts online. Why? Your first e-mail address is for friends, family and people who you trust to send you real e-mails. The second account you create can be given to anyone/any company online. This way, if these companies spam you, it won’t interfere with your personal e-mail account, and if the spam ever gets too bad, you can just create a new second account, and not have to tell all your friends to use a new e-mail address.
Comments Off on Step By Step New Hotmail Account Guide
May 28 2010
Shoplifters To Terrorists
Another vague tie in to Call Of Duty: Modern Warfare 2 again (a game I’ve been playing recently), as I came across a piece on high tech surveillance techniques that could be in use on battlefields within just a few years.
The fact that this concerns me less than behaviour-analysing CCTV systems that were touted in the last couple of years for domestic use is probably a purely selfish instinct. I’m not likely to ever find myself in a potential war zone, whereas the thought of being flagged for a higher level of scrutiny whilst wandering around a UK high street or shopping centre creeps me out a little. The end results should dictate a reversal of concern levels though – after all, if a security guard/policeman takes an interest in my shopping in Cheltenham or Swansea, I’m never going to encounter a predator missile suddenly being aimed at me. If the software or operators make a mistake in Afghanistan/Pakistan though, the error could lead to loss of life, not just an inconvenience.

The MW2 reference was that the article originally caught my attention as one of the photos reminded me of a level I’m trying to complete right now. Hopefully DanD will be able to come over again soon, as playing with two controllers isn’t particularly easy.
Comments Off on Shoplifters To Terrorists
May 28 2010
List Too Long For A Tweet
Unless you are @janeslee, or have a particular interest in which books I’ve read in the last three or so weeks, you can probably safely ignore this post. If you are janeslee, do I know you in real life?
I just noticed that you were in Wales, and despite my current location being Astana, Kazakhstan, we are based in Swansea when we are back in Britain.
Anyway, as you may guessed, my answer to your query of “what you reading that’s keeping you intrigued?” wouldn’t fit within 140 characters, so I’m writing this here and will reply to your tweet with a bit.ly link to this post.
John Birmingham – Final Impact
Jasper Fforde – Something Rotten
David Gerrold – The Man Who Folded Himself
Arkady and Boris Strugatsky – Destination: Amaltheia
Arkady and Boris Strugatsky – The Final Circle of Paradise
Arkady and Boris Strugatsky – Prisoners of Power
Arkady and Boris Strugatsky – Roadside Picnic
Arkady and Boris Strugatsky – The Time Wanderers
Arkady and Boris Strugatsky – Poor Cruel Folk
Arkady and Boris Strugatsky – Monday Begins On Saturday
Arkady and Boris Strugatsky – The Gigantic Fluctuation
Arkady and Boris Strugatsky – Spontaneous Reflex
Arkady and Boris Strugatsky – Probationers
Harry Turtledove – The Man With The Iron Heart
I haven’t found a very well stocked English book shop here in Kazakhstan suddenly, these were all read on my MP4 player than can read plain TXT files. (Obviously I own all these books in paper form back in the UK, and wouldn’t dream of downloading e-books otherwise… /end-arse-covering)
May 26 2010
Recorded Strokes And Missing Blocks
Sounding more like a plot device in Mission Impossible XIV than a well researched BBC article, spying on people’s keyboard strokes via the mains cable that powers the computer is more fuel for the tin foil hat brigade. The article doesn’t mention whether PS/2 keyboards are the types of device that can leak information back through to AC wiring (not at all sure why, but I can imagine there being less potential digital interference when USB was used), nor does the piece refer to whether PSUs with certain features would be likely to curtail this activity. For that matter, would surge suppressors (with their sine wave cleaning abilities) further protect paranoid users?
Another article with potentially information missing, is a piece on credit card info thieves using cloned cards at unattended checkouts in supermarkets to empty American customers’ accounts. I can’t understand why a simply block on non Chip’n’PIN cards using these sort of self service checkouts wouldn’t be put in place. This way staff would get a chance to physically check the card at normal check outs, meaning more hassle for the data thieves at the very least.
Comments Off on Recorded Strokes And Missing Blocks
May 26 2010
Late Spring Clean
After repairing all my other websites (following the hacking of my server and insertion of malware links), I decided to standardize all the plugins across the sites, and only install themes and plugins that were available from the official WordPress repository. This makes keeping them up to date a lot easier (and semi-automatic) and should any new hacks take place, the clean up job will be quicker. In the last few days, I also finally re-instated the Amazon links; when these sites were not built around WordPress, I’d had Amazon.co.uk books related to each topic displayed, but didn’t see a single sale. I went through my AWStats information, and nineteen out of twenty sites had the most traffic from America. (Actually Russia figured quite heavily as well, but a) Russian visitors aren’t famous for click on adverts and buying products and b) Amazon don’t have a .RU specific site, oh and c) A lot of the Russian visitors were actually spam bots, once again not known for earning web masters money 🙂 ) So, discovering that I had already set up an affiliate account there, I went ahead and inserted Amazon.com adverts on each site. I’m hoping that the sites will start to earn a bit money than the last year’s income, though I know that with summer coming there will be the usual dip in visitor numbers and corresponding income. The grill (BBQ) tips site might just be the exception, I suppose 🙂
Comments Off on Late Spring Clean
May 26 2010
Grey Hat Hackers That Aren’t Active
Who can tell what has changed in the last 11 months, but officially (see this article), the British government has the means to carry out cyber-attacks, but does not use them for industrial espionage. Whilst giving this explanation, it was made pretty clear that the UK believes China and Russia (amongst many others, I’m sure) do illicitly obtain information to assist national or major companies in their respective territories. Whether government employees or private contractors do this in Britain is not really a argument for most I think, but it would be interesting to hear the excuses given if Lord West was caught out and somehow such commercial spying was ever traced back to officially sanctioned groups or individuals.
Comments Off on Grey Hat Hackers That Aren’t Active
May 24 2010
Stoned Wallabies And Decoy Spiders
Continuing the clearance of old news stories and images that have been stuck in draft posts for a while, here we have a couple of articles from the BBC. The first is about stoned (although to me that only infers weed, not the other substances mentioned) wallabies creating crop circles see here. Whether they would ever approach the geometric designs that some (in)famous hoaxers in Britain did is highly arguable, and I would have loved to have seen some aerial shots of the damage done/art dislpayed by the wallabies. Also worth a quick scan are the mostly tongue in cheek comments at the end of the article.
With the second article we have a species of spider that builds life-sized decoys to distract predators from eating the real McCoy. I also seem to remember an old article in New Scientist on how spiders under the influence of different substances spun a wide variety of altered web patterns, but I can’t seem to find the bookmark or draft post for that.
« Previous Page — Next Page »